How do you picture a digital bread crumb? Is it a memorable mixture of letters, numbers and characters enabling you to access a favorite social network? Or do you visualize it as a unique image overlooking a personally designated caption that’s identifiable only by you? Is the bread crumb seasoned by one or more private security questions required to gain bank account access? Although the digital traces we leave behind establish a permanent trail of our internet life’s daily A to B, we do not have the luxury of said traces crunching beneath our feet and reminding us that they are there to stay…unless we take the initiative and learn the necessary cyber security skills to say otherwise.
Should you decide to take the initiative and develop competent cyber security skills, there’s no better time to do so than October, America’s National Cyber Security Awareness Month.
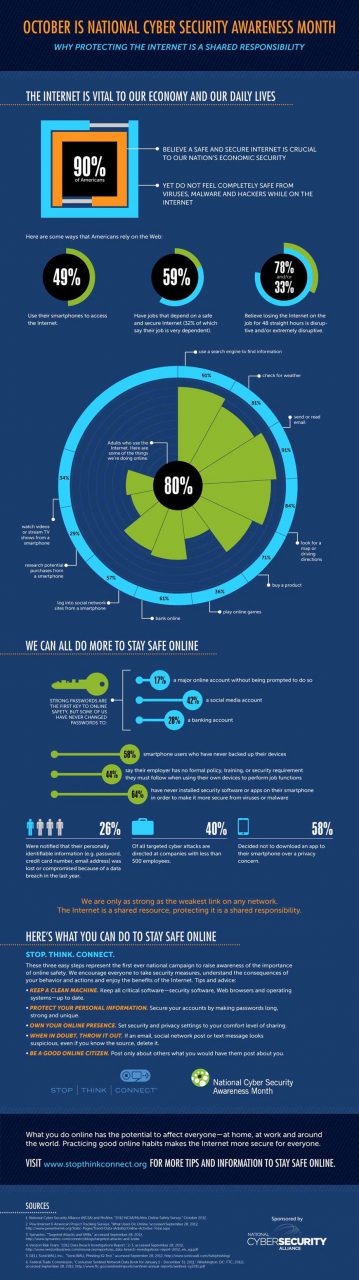
What Is Cyber Security Awareness Month?
As much pride as we take in The United States being founded as a country that protects and encourages basic human liberties, our freedom to create and to innovate has ironically limited our ability to maintain those simple liberties in the face of those preying upon our collective complacency. In other words, the more we have, the more we have to lose. Consequentially, our principal vulnerability lies exposed as an undressed flesh wound, at the mercy of the highest bidding bacteria, in the hands of our communally craved digital funhouse: the Internet.
Established as a response to the nation’s increased dependency upon internet technology, National Cyber Security Awareness Month (NCSAM) creates events and initiatives in order to raise public and private sector awareness of cyber security as a means to construct formidable national resiliency against potentially crippling cyber crime. Sponsored by The Department of Homeland Security (in collaboration with the National Cyber Security Alliance and the Multi-State Information Sharing and Analysis Center), National Cyber Security Awareness Month takes place in October every year and is currently celebrating its eleventh year of operation.
Founded upon the belief that critical infrastructure and digital technology are prime national security priorities, and that cyber security is a “shared” responsibility in The United States, the NCSAM program is spread out across five distinctly themed weeks geared towards educating the nation and its individuals in methods of assessing threat to infrastructure, economy, finances, privacy and identity. Participation in NCSAM is open. One may participate in any or all of the events of the five week program, which operates upon a thematically blocked structure specifically catering to different attendees motivated by different needs.
Themes of the NCSAM program include promoting online safety via simple steps to secure internet access (Week One), building efficient security into information technology products (Week Two), the importance of protecting critical infrastructure and properly securing all internet-connected devices (Week Three), cyber security tips for small to medium-sized businesses and entrepreneurs (Week Four) and working with law enforcement to teach the public how to prevent cyber crime victimization (Week Five).
Cyber Security Breaches and Why Awareness is Important
The internet has become a global safe haven for human beings, an infinite stack of sandbags we retreat behind when fleeing our mutually mundane anxieties and concerns. It’s a post-modern rocking cradle of sorts. Therefore, because we feel safe online, we willfully throw everything about ourselves into the constantly crunching jaws of the information superhighway: addresses, photographs, daily journal entries, bank accounts, credit card payments, social security numbers, medical records, insurance claims, harbored grudges, personal vendettas, sexual escapades, marital infidelities and the list goes on . . . Naturally, because the information we disseminate onto the digital landscape is occasionally (or often) extremely sensitive, predators sit idly, eyes between bush branches, waiting to lodge their foot between a backdoor that we didn’t close quite quick enough.
This past summer, in June of 2014, a cyber attack on JPMorgan Chase jeopardized the accounts of 76 million households and seven million small businesses. Hackers who orchestrated the attack reached more than 90 servers during their breach and acquired the most secure administrative privileges of several dozen of the previously mentioned servers. Although JP Morgan account holder addresses, phone numbers and emails were accessed by hackers, their financial information, including passwords and Social Security numbers, remained secure. Regardless of the minimal fallout, as a result of the intrusion JP Morgan is forced to change security programs and to renegotiate licensing deals, which may allow hackers an opportunity to excavate the current JP Morgan system for any other gaping holes. While JP Morgan plans to spend 250 million dollars annually on improving digital security, the most recent cyber intrusion remains a concrete demonstration of Wall Street’s susceptibility to cyber crime despite its repeated, costly efforts to thwart digital victimization.
Being that not every United States citizen is a JP Morgan account holder invested in the competency of the company’s cyber security construct, the June 2014 JP Morgan cyber attack may not necessarily strike concern in the hearts of the general American public. However, to ignore the nationwide implications of the JP Morgan breach would be a mistake for any American citizen dependent upon even the simplest mediums of financial management, such as a bank account or a credit card. It was only last year that Target and Home Depot, both widely popular American retail shopping spots, suffered cyber attacks that compromised the information of several million customers and cardholders, including 56 million Home Depot cardholders, 40 million Target cardholders and 70 million other Target customers. Clearly, no entity involved in digital financial transactions, whether group or individual, is immune to hammer of cyber crime’s iron fist.
Tips for Maintaining Formidable Cyber Security
Being that the threat of cyber crime and cyber terrorism continue to strangle our sense of security (with no sign of fingers peeling), the natural consequence of this increasing digital demand has assumed the form of a budding cyber security consultation market. Currently, several sources offer professional advisement on effective cyber security tips geared towards technology-dependent organizations and individuals. Security advisors include Department of Homeland Security-sponsored organizations such as the 24/7 incident responding United States Computer Emergency Readiness Team (US-CERT) and the educationally engaged National Cyber Alliance-powered StaySafeOnline.org, the latter of which espouses a focus on prevention, resolution and restitution.
Despite several cyber security consultant entities emphasizing a focus on the digital integrity of multi-layered organizations, various other experts stress educating individuals on the risks of personal cyber security tactics. Paul Moore, Program Officer of the social justice-funding David Bohnett Foundation, manages a program consisting of 61 LGBT-serving computer labs nationwide. The computers are publicly used and provide a virtual revolving door of users accessing sensitive personal data throughout any given day. Being that there are predators seeking to take advantage of user complacency, Moore suggests strict discretion to any user operating a public computer. “You want to secure your personal information . . . don’t save login information, erase any information you’ve used on the computer and clear your web browser too. Be diligent about protecting sensitive information.”
The depth and complexity of effective cyber security may initially appear overwhelming to anyone not rigorously invested in its textured methods and continued development. However, adopting even the simplest personal precautions provides one with a seedling sense of comfort and a baseboard to fuel the growth of engagement in practicing adequate digital defense. In other words, embracing proficient online security strategies is, as National Cyber Security Awareness Month emphasizes, a shared responsibility of all network-connected United States citizens.